This is the conclusion of my three-part series on Hyperledger Sawtooth Security. I started with Sawtooth consensus algorithms in part one, then continued with Sawtooth node and transaction processor security in part two. Here I will conclude by discussing Sawtooth application security and Sawtooth network security.
Client Application Security
The client part of a Sawtooth application is written by the application developer. The Sawtooth client communicates with a Sawtooth node by REST API requests, including signed transactions and batches. The signing is performed with a private key and, as such, key management and security is important. With Bitcoins, for example, poor key management has resulted in stolen Bitcoins and a “graveyard of Bitcoins” that are inaccessible forever. Key management is the responsibility of the client application as keys are not managed by Sawtooth software.
A keystore is where you securely store your keys. The public key for a keypair, used for signature verification, can be and should be distributed to anyone. The private key portion, used for signing, must be safeguarded from access by others. Here are some keystore methods, ordered from low to high security:
- The minimum security used should restrict access to the private key. That is either restrict access to the machine holding the key or restrict read access to the private key file to the signer or (better yet) both
- Better protection would be the use of software-encrypted keystore. This would be a private keystore accessible by a PIN
- The best protection is from a Hardware Security Module (HSM) keystore or a network-accessible key manager, accessed using the Key Management Interoperability Protocol (KMIP)
Client Authentication
A Sawtooth client may take external user input. In which case, it is important to authenticate that the user is who they say they are. Authentication methods are usually categorized, from low to high security, into:
- Single-factor Authentication (SFA). SFA is something you know. It could be something like a PIN, password, passphrase, or one-time password (OTP). The main disadvantage with SFA is it could be weak or hard to remember
- Two-factor Authentication (2FA). 2FA is SFA plus something you have. It could be a security key, such as a U2F token (e.g., YubiKey). The main disadvantage with 2FA is it can be lost or stolen

- Three-factor Authentication (3FA). 3FA is 1FA and 2FA plus something you are (biometrics). Examples include fingerprints, face recognition, or retina scan. The main disadvantages with 3FA is it can be forged and cannot be easily changed
With 2FA and 3FA, the idea is defense-in-depth (i.e., multiple hurdles to authenticate).
Network Security
Blockchains are subject to Distributed Denial of Service (DDoS) attacks. That is, an attack that attempts to overload blockchain nodes by flooding the targeted nodes with bogus messages. Classical public, unpermissioned blockchain networks avoid DDoS attacks because transactions require spending digital currency (such as Bitcoin), making attacks costly. Also, public blockchain networks are highly distributed—with thousands of nodes—making a DDoS attack on the entire network impractical.
Private or permissioned blockchains, such as Sawtooth, are not designed to run on a public network. As such, they do not require digital currency and “mining.”
Sawtooth network can and should be mitigated against DDoS attacks as follows:
- Back pressure, a flow-control technique to reject unusually frequent client submissions. If the validator is overwhelmed, it will stop accepting new batches until it can handle more work. The number of batches the validator can accept is based on a multiplier (currently two) of a rolling average of the number of published batches.
- Sawtooth communication uses the Zero Message Queue (ZMQ or 0MQ) message library. Sawtooth optionally enables encryption with ZMQ when the network_public_key and network_private_key settings are defined in validator.toml. For production, generate your own key pair instead of using a predefined key that may be present.
- REST API input is validated to avoid buffer corruption or overflow attacks.
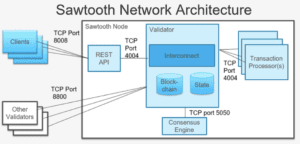
- TCP port 4004, used for communication between internal validator node components, should be closed to outside access in any firewall configuration,
- TCP port 5050, used to communicate between the validator node and the consensus engine, should be closed to outside access in any firewall configuration.
- TCP port 8008, used for the REST API, should be closed to outside access in a firewall configuration providing all application clients accessing the REST API come from the local host.
- If you use the Seth TP (for WASM smart contracts), TCP port 3030, used for Seth RPC, should be closed to outside access in a firewall configuration, providing all RPC requests come from the local host.
- TCP port 8800, used to communicate between validator nodes, must be open to outside access in any firewall configuration.
Sawtooth validator nodes should be deployed on a VPN or other private network to prevent any outside access to Sawtooth TCP ports.
Basically, best practices dictate closing as many network ports as possible, encrypting network communications, and deploying in a protected network environment (such as a VPN).
Further Information
- Sawtooth documentation: https://sawtooth.hyperledger.org/docs/core/releases/latest/
This includes a Sawtooth overview, development, design, etc. It includes PoET specification and PoET implementation with SGX. Tutorials show installation and running a sample application. - PoET overview: https://medium.com/kokster/understanding-hyperledger-sawtooth-proof-of-elapsed-time-e0c303577ec1
- SGX overview: https://software.intel.com/en-us/sgx
- Materials for a (future) intermediate course, Sawtooth for Application Development, is at https://github.com/hyperledger/education-sawtooth-simple-supply. Modules 2-3 include security topics.
- Transactor Key and Validator Key Permissioning (Video, 2017, by Andrea Gunderson, Bitwise) 20171005-sawtooth-tech-forum.mp4 https://drive.google.com/file/d/0B_NJV6eJXAA1R3BLQlZsM2xMMTg/view
- Hyperledger Sawtooth Security Audit (Pre-release, 2017): https://www.hyperledger.org/blog/2018/05/22/hyperledger-sawtooth-security-audit
- Hyperledger Blockchain Security Video (free registration): https://gateway.on24.com/wcc/gateway/linux/1101876/1668381/blockchain-and-the-enterprise-but-what-about-security
- Git source repository: https://github.com/hyperledger/sawtooth-core
- Chat: https://chat.hyperledger.org/channel/sawtooth
- Unofficial FAQ: https://github.com/danintel/sawtooth-faq
Sign up for the monthly Hyperledger Horizon & /dev/weekly newsletters
By signing up, you acknowledge that your information is subject to The Linux Foundation's Privacy Policy